In recent years, the fast-growing smart automotive industry encounters new challenges similar to those in "traditional" computer security.
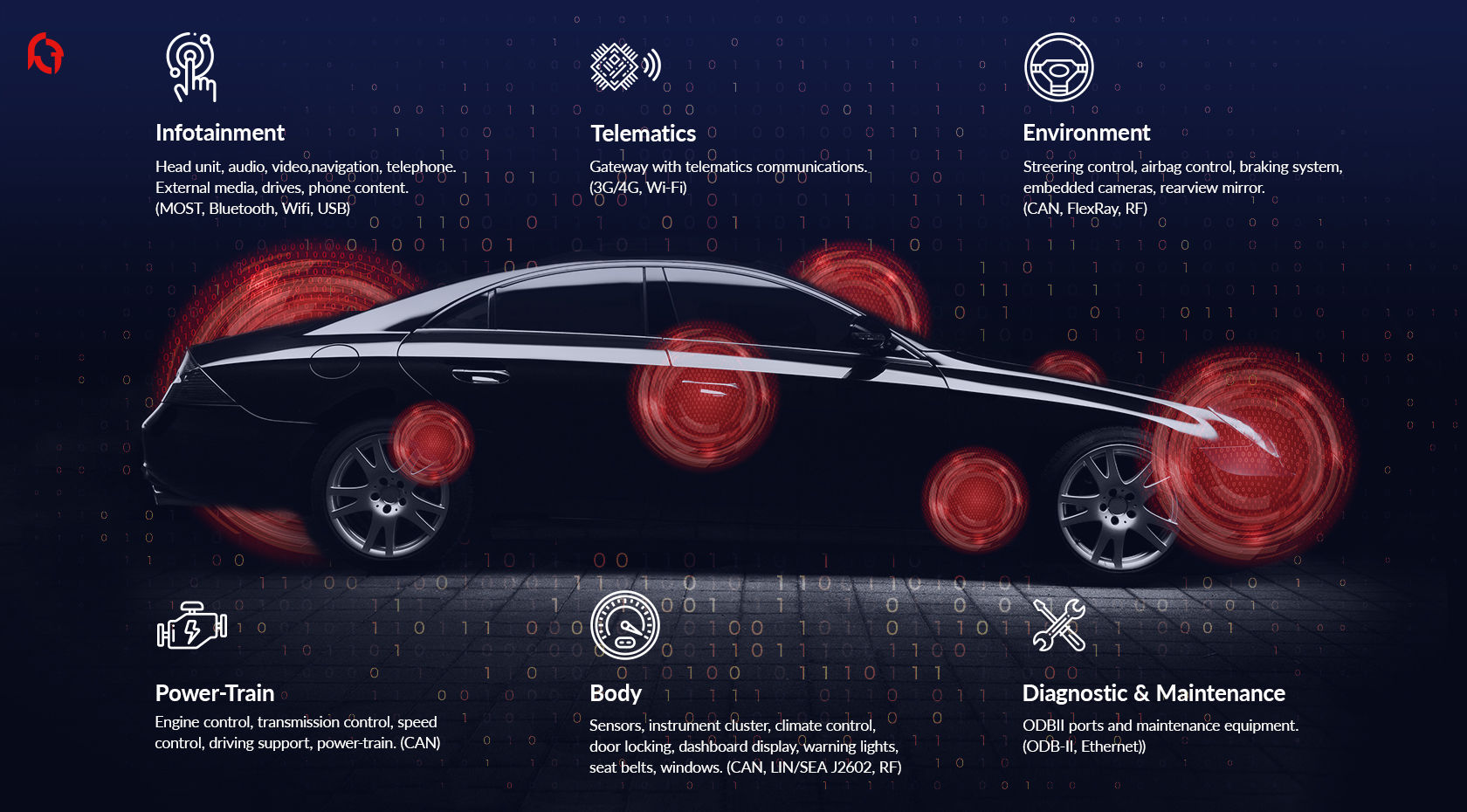
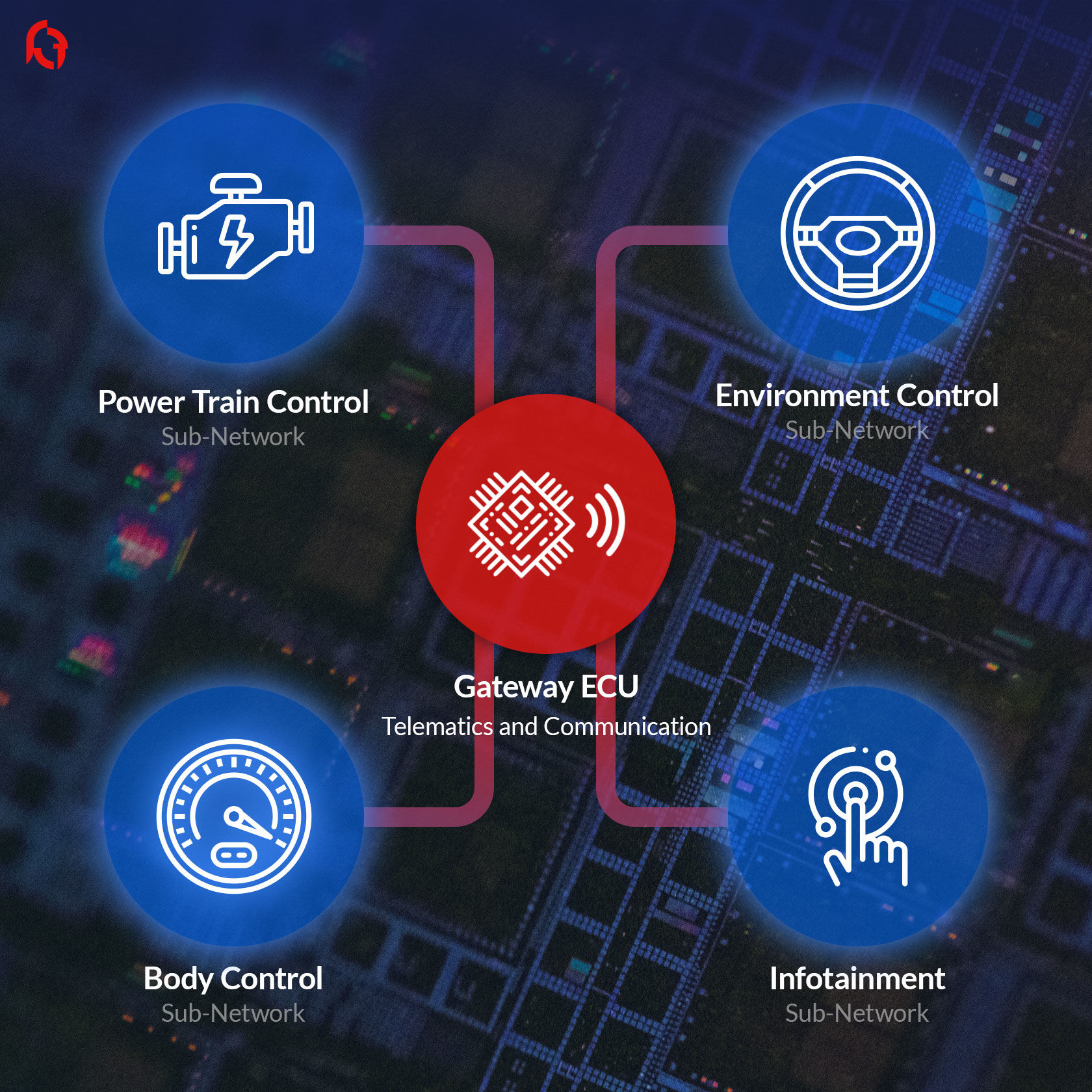
To improve car safety or enhance car users' experience, the modern automobile is composed of many sub-networks operating in different domains.
Such in-vehicle sub-networks connect different sensors and several Electronic Control Units (ECUs) that use various protocols to exchange data transported by different bus systems (Ethernet, CAN, LIN, FlexRay, MOST etc.).
Furthermore, modern cars and commercial vehicles have been equipped with Internet-connected infotainment system and Telematics Control Units which integrates multiple wireless communication systems (Cellular, Bluetooth, Wi-Fi, etc.).
Each of these components require appropriate protection, since its compromise may strongly impact the privacy, the security or even the safety of the end users.
Research shows that remote attacks can be feasible utilizing complex chains of vulnerabilities in different vehicle components.
Such in-vehicle sub-networks connect different sensors and several Electronic Control Units (ECUs) that use various protocols to exchange data transported by different bus systems (Ethernet, CAN, LIN, FlexRay, MOST etc.).
Furthermore, modern cars and commercial vehicles have been equipped with Internet-connected infotainment system and Telematics Control Units which integrates multiple wireless communication systems (Cellular, Bluetooth, Wi-Fi, etc.).
Each of these components require appropriate protection, since its compromise may strongly impact the privacy, the security or even the safety of the end users.
Research shows that remote attacks can be feasible utilizing complex chains of vulnerabilities in different vehicle components.