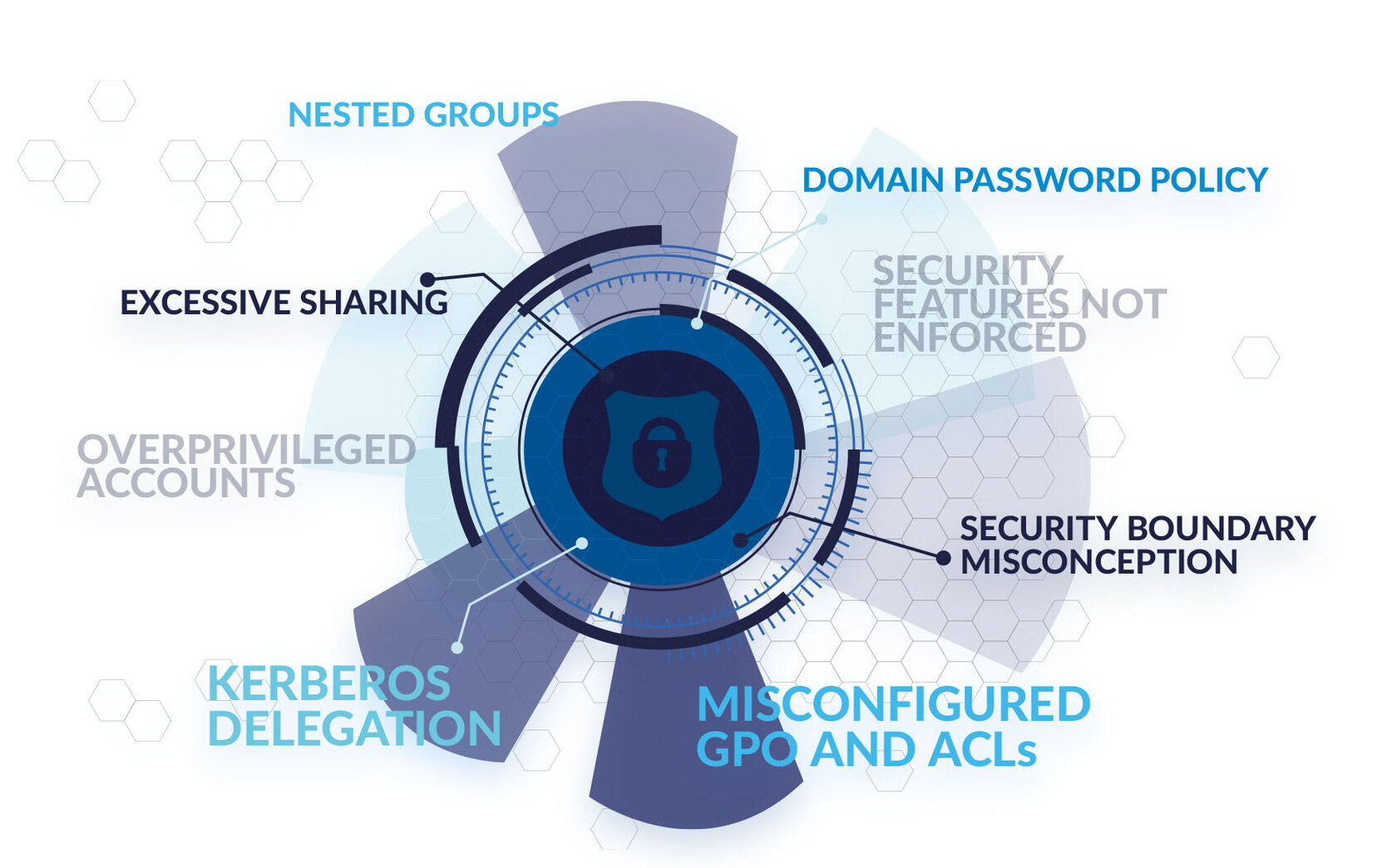
Active Directory (AD) is the Microsoft enterprise product adopted by the majority of the companies to manage their internal directory-based and identity-related services.
In a Windows-based environment, almost every application is integrated with Active Directory for authentication, resource access, and single sign-on. It is one of the most critical components of an enterprise IT infrastructure.
It is not surprising that AD is a prime target in cyberattacks.
Installing the latest security patch does not mean having a secure system. More and more adversaries' strategies are leveraging misconfigurations to compromise internal networks and perform malicious activities.
The Active Directory deployments of most organizations are insecure and vulnerable to known exploits, but even if a company has a fully patched environment, administrators have to deal with complex sets of different configurations. Due to lack of time and misleading tools, even seasoned IT administrators deploy insecure configurations that could lead to potential breaches.
In a Windows-based environment, almost every application is integrated with Active Directory for authentication, resource access, and single sign-on. It is one of the most critical components of an enterprise IT infrastructure.
It is not surprising that AD is a prime target in cyberattacks.
Installing the latest security patch does not mean having a secure system. More and more adversaries' strategies are leveraging misconfigurations to compromise internal networks and perform malicious activities.
The Active Directory deployments of most organizations are insecure and vulnerable to known exploits, but even if a company has a fully patched environment, administrators have to deal with complex sets of different configurations. Due to lack of time and misleading tools, even seasoned IT administrators deploy insecure configurations that could lead to potential breaches.